Over the last 48 hours, the security world has been shaken by a report from Anthropic, detailing how Claude has been used to design, orchestrate, and execute sophisticated cyber campaigns. Their findings echo what we’ve already seen in the most recent OpenAI, Anthropic, and Google Threat reports.
Attackers are using Claude and other LLMs to massively boost their productivity and effectiveness. Importantly - they are doing so in ways that bypass existing detections.
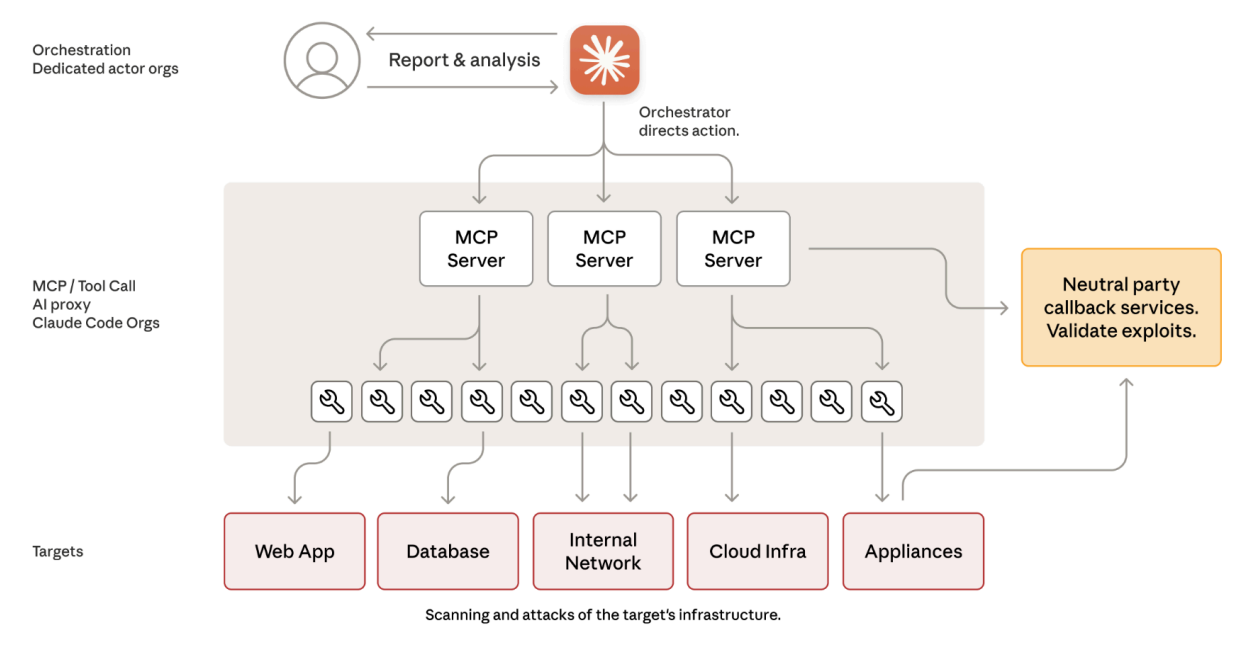
AI powered attacks are not hype. They are happening now and accelerating. They’ve hit the front page of the Wall Street Journal this week thanks to Anthropic’s report. In 2026 they’ll be on the mind of most American executives, entrepreneurs and security teams.
It is predictable. I should know, as we at DeepTempo predicted the rise of AI powered attacks and spent over two years investing millions of dollars, assembling a cyber and deep learning team, and building a LogLM based solution with the help of design partners like BNY and various tier one telcos and national security collaborators to be able to detect, isolate and assist in the response to exactly these sorts of attacks.
Review: What have we learned about the use of LLMs by Attackers?
A few overlooked highlights from the OpenAI, Google Threat Center (Gemini), and Anthropic reports that stood out to me:
- LLMs raise the capabilities of less sophisticated threat actors, who now have access to solutions that were once limited to advanced persistent threats. The take away from Anthropic’s report shouldn’t be: look at what China did; it should be: look what any reasonably committed attacker can now do.
- LLMs accelerate activities to a pace that humans cannot match. For example, they perform research and reconnaissance, generate hypotheses about what next steps to make, and then make them. The report highlights that multiple operations were occurring per second.
- LLMs orchestrated attacks avoid most security detections; as one of our researchers here at DeepTempo put it, these LLMs couldn’t author the same attack path and specific exploit exactly the same way twice even if you asked them to. This makes already hard to discern “living-off-the-land” (LOTL) maneuvering and command and control communication even harder to detect. Novel attacks are nearly impossible to see via rules based detections.
- EDRs failed to detect these attacks thanks to the use of LoLT techniques and novel approaches; some of the best technology in cybersecurity works at the end point, attempting to form a perimeter at the edge. Unfortunately the attackers profiled by the report mostly used open source utilities to gain access; this LoLT pattern is classified as benign by systems that are unable to see beyond particular signatures to discern the intent of the behavior.
These reports confirm what recent data on the quantity of attacks and the speed that vulnerabilities have strongly suggested - attackers are becoming massively more productive and sophisticated.
The good news is that there is a path forward leveraging AI and building upon investments made from the SIEM to the data lake to radically improve the speed, adaptability, and focus of our defenses.
Identifying LLM orchestrated attacks - with a special sort of AI
This is exactly why DeepTempo exists.
We founded DeepTempo because we saw this moment coming. The already fragile state of cyber security was about to get much worse.
Years before today’s reports, we recognized a coming asymmetry:
- Attackers would soon use LLMs to generate novel, signature-evading, LOTL-based, multi-hop behavior.
- Traditional rule-based and SIEM-centric detection would not enable their users to move fast enough to counter a flood of innovative and adaptive attacks.
- Many customers were investing in Snowflake and Cribl and other solutions as a data layer for security. While these investments were often made to save costs on legacy SIEMs, we realized the same data lakes could be used to run AI powered threat detections.
Not all AI is well suited to detecting AI attacks
After talking with large enterprises, service providers, friends in cybersecurity, and investors, we realized that modern detection requires a deep learning foundation model — a system that can learn the behavioral patterns behind attacks and generalize to new ones without rules, signatures, or human tuning. The result is DeepTempo’s LogLM, our purpose built proprietary model pretrained on the ground truth of real system behavior instead of handcrafted features or narrow, point-in-time ML models. We built a foundation model that can adapt quickly, in many cases immediately, to different customer environments by applying what it has learned in prior environments and from its pretraining. We started with flow logs as the representation of this ground truth because while you can spoof or avoid end point detection in a variety of ways (especially if you are able to use something like Claude) you cannot avoid touching the network. And we realized that once we got really good at seeing lateral movement and command and control and other common patterns then we could detect, classify, and help to isolate and counter almost all flavors of attacks.
DeepTempo’s LogLM today appears to be unique in cyber security, most similar to approaches such as Stripe’s anti-fraud foundation model.
LogLM is:
- A deep, self-supervised foundation model trained on tens of billions of flow logs.
- Able to see novel attacks, not only known patterns, and to then map those attacks to the most similar MITRE ATT&CK.
- Able to detect LLM-assisted behavior chains, including distributed reconnaissance, beaconing rotation, stealthy lateral movement and quiet exfil.
- Enormously scalable and efficient to run, very approximately 100k more efficient than attempting to use a LLM directly to see threats in streams of logs.
- Extends the value of existing investments in data lakes and SIEMs.
DeepTempo is available preintegrated into your Snowflake, Cribl and other environments - able to send information into your SIEM and Slack about the sorts of attacks Anthropic’s report highlights.
Next Steps
As we build and deliver our AI based LogLM platform for threat detection, we invite every defender, every detection engineering leader, every CISO, and every partner, including our friends in the AI SOC world, to join us in our journey. Check out what a tier-1 telco discovered with DeepTempo.
We’re also offering assessments to help you evaluate DeepTempo against your existing flow data to see what you might be missing. Get in touch with us as you plan for the next year.
Happy hunting.

